In today’s cloud-native world, security is paramount. It’s not enough to secure applications only during deployment; runtime security is crucial. Falco, a CNCF-hosted, open-source security tool, helps detect threats in real time across hosts, containers, Kubernetes, and cloud environments.
What is Falco? #
Falco is a cloud-native security tool that helps in detecting the threats in real time. It can detect threats across hosts, containers, Kubernetes & cloud environments. Falco uses the eBPF technology that continuously monitors the events (such as Linux syscalls), and reports for any suspicious activities like abnormal behaviours, potential security threats and compliance violations from apps by triggering the alerts to the team. It’s an open-source CNCF project originally developed by Sysdig.
Why Use Falco? #
Falco offers several advantages for runtime security:
- Real-time threat detection: It can detect threats like reverse shells, RBAC abuse, and file access.
- Lightweight and powerful: Falco leverages eBPF for efficient monitoring.
- Highly customizable: You can tailor Falco rules to your specific needs.
- Versatile: It supports various event sources.
- Easy integration: Falco integrates seamlessly with alerting systems like Slack and webhooks.
How Does Falco Work? #
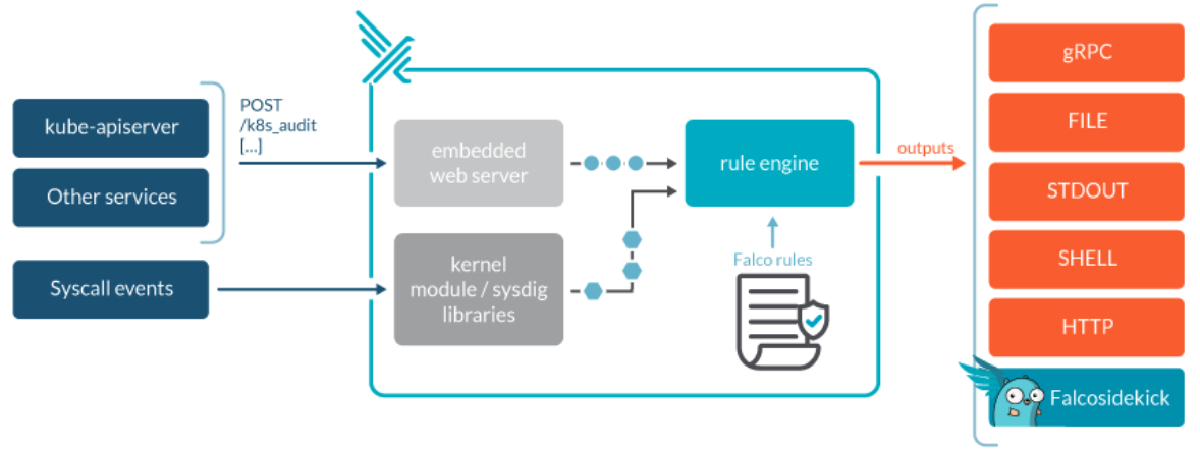
Falco continuously monitors the event sources, reporting any suspicious activities or potential security threats based on the defined Falco rule. If any of the Falco rule is evaluated to true by the Falco Engine then the event is send as the Falco outputs. By default, Falco performs a standard output of such events which can then be configured to send it to Slack (over HTTP/S), gRPC protocol, file outputs, etc.
Falco Event Sources #
Falco intelligently monitors events from various sources:
- 🧠 Linux SysCalls: Observes low-level system activity using Kernel Modules or eBPF.
- ☸️ Kubernetes Audit Logs: Detects unauthorized access attempts and resource manipulation.
- 📦 Container Lifecycle: Monitors container start, stop, and execution events.
- ☁️ Cloud Provider Logs: Ingests logs from cloud providers like AWS CloudTrail.
- 🔧 Custom Event Sources: Supports additional custom event sources.
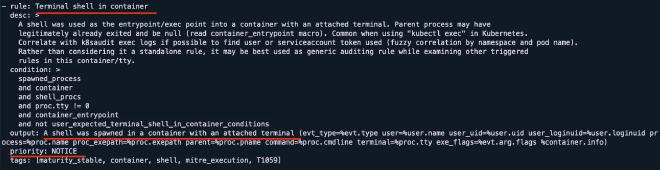
Falco Rules #
Falco Rules are the core of its detection mechanism. These YAML-based rules define the suspicious anomalies to detect. The Falco Rule Engine evaluates these rules, raising alerts based on syscalls and metadata. You can use predefined rules or customize them to meet your specific security requirements. A Falco rule consists of several components:
- rule: Name of the rule
- desc: Description of the behavior
- condition: Logical expression based on syscalls and fields
- output: Alert message format
- priority: Severity Level
- tags: For organizing the rules
Sample Falco rule:
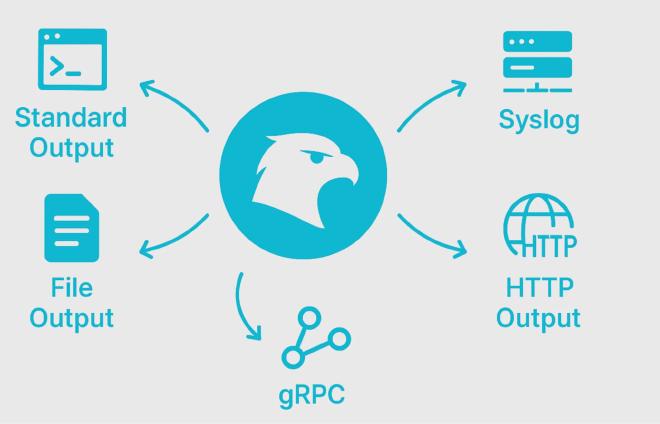
Falco Outputs #
Falco generates outputs that can be used for alerting and further analysis. By default, Falco sends as a standard output.
Falcosidekick #
Falcosidekick is a companion tool that acts as a central endpoint for Falco instances, forwarding events to external systems. It can run as daemon process, or can be deployed in Kubernetes cluster.
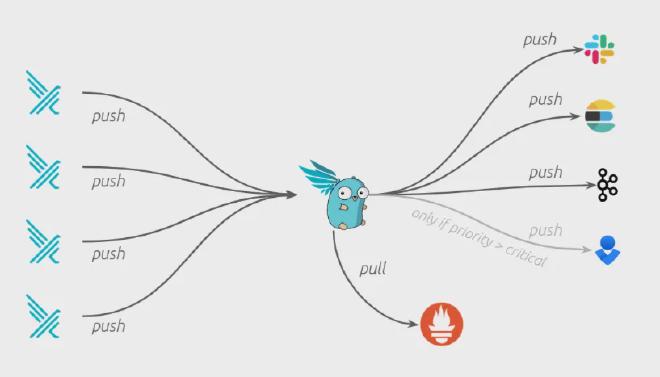
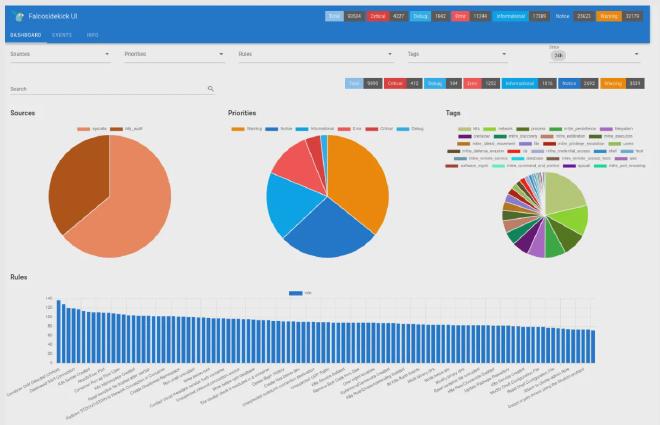
Falcosidekick UI #
Falcosidekick UI provides visualization for real-time event monitoring and analysis to the Falco Events using a centralized user-friendly dashboard.
- Real-time Event Monitoring
- Advances search and filtering options
- Categorized view based on priority, source, rules
- Integration Support with third-party services like Slack, etc
- Simplifies incident response workflows
Demo: Falco in Action #
In this demo, a custom rule of Falco has been configured to detect if a pod is reading the senstive files or not in a Kubernetes cluster. And when a suspicious pod violates the defined rule then the Falco Engine detects the event and forwards it to the Slack by Falcosidekick. All these events can also be then visualized using the dashboard of falcosidekick-ui.
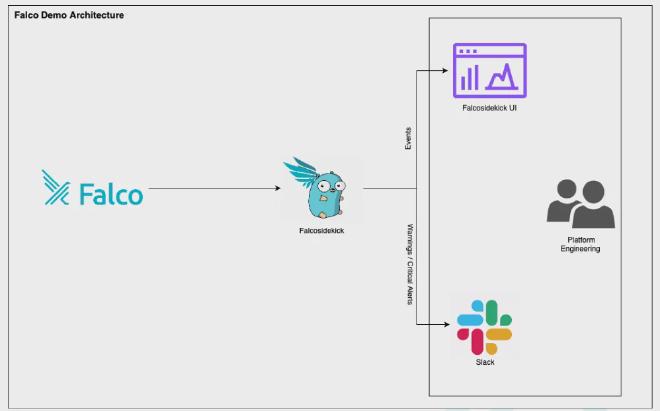
Please note the recorded demo can be found in this link and the source code in the given GitHub repository. https://drive.google.com/file/d/1Svv0lSg4_Xgf6cVzdXJeduvUmRqtkQRy/view?pli=1
Limitations and Challenges of Falco #
While powerful, Falco has some limitations:
- 🧠 Kernel dependency: It relies on the Linux kernel.
- ⛔ Detection, not prevention: Falco only detects anomalies, it doesn’t prevent them.
- 🔔 Potentially noisy alerts: Rules need careful tuning to avoid excessive alerts.
- 🪟 Limited Windows support: Primarily focused on Linux.
- 🛠️ Rule management: Custom rule writing requires expertise.
Reference Links #
- Falco Documentation: https://falco.org
- GitHub Projects: https://github.com/falcosecurity/falco
- Falco Rules: https://falco.org/docs/concepts/rules/
- Falco Installation on Kubernetes: https://falco.org/docs/setup/kubernetes/
- Falcosidekick: https://github.com/falcosecurity/falcosidekick
- Falcosidekick UI: https://github.com/falcosecurity/falcosidekick-ui
- Demo Recording & Code: https://github.com/vinod827/cloudkit-lab/tree/main/iac/k8s/falco
Secure your Kubernetes environment before it s too late — with Falco, you can stop threats before they become disasters.
– Written by Vinod Kumar